Data protection day is an opportunity to take stock of the regulations governing sensitive information systems and more specifically, Restricted Ditribution (RD). What are the technical practices to adopt if your organization or architectures host data at the “RD” level? Interdepartmental instruction II 901 in practice.
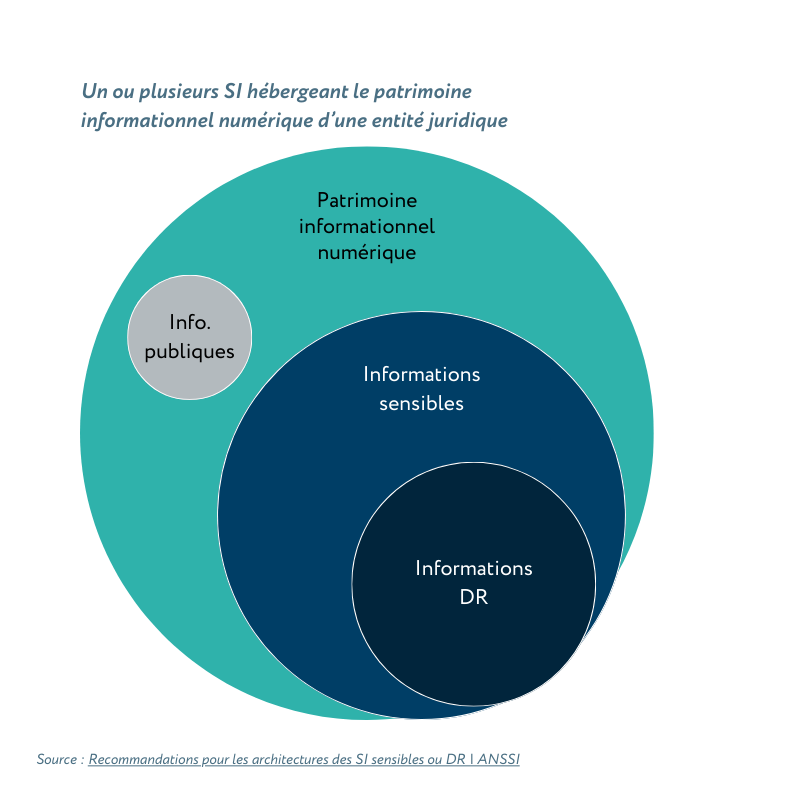
Let’s start by defining what is “sensitive information”. As specified by the ANSSI[1], this is information “whose disclosure to unauthorized persons, alteration or unavailability are likely to undermine the achievement of the objectives of the entities that implement them.”
The protection of this data is based on 3 pillars: confidentiality, integrity and availability, for example in case of an IS attack using a ransomware.
As a subset of sensitive data, the RD (“Restricted Distribution”) information is specifically mentioned. It may be exploited by state administrations, organizations under the PPSTN (data that can be misused for terrorism or proliferation of weapons of mass destruction), or by service providers who collect this data and are qualified by ANSSI.
Access to RD information is strictly reserved for persons “with a compelling need to learn about it in the course of their duties or specific mission”.
RD information can only be processed on a RD-approved Information System and is subject to regulations that impose specific security measures.
Three classes of Information Systems
L’II 901 définit trois classes de Systèmes d’Information :
- Class 0 IS a public IS (e.g. Internet) or IS connected to a public IS that does not meet the requirements of Class 1
- Class 1 IS is a sensitive IS (or RD) connected to the Internet through a secure gateway that meets the security requirements defined in II 901;
- Class 2 IS a sensitive IS (or RD) physically isolated from the Internet
Sensitive or DR IS: technical and organizational security measures
The II 901 recommendations and rules framed by the ANSSI are intended to guarantee the protection of sensitive IS, and in particular of IS classified as “Restricted Distribution” (RD).
The main measures to be taken are:
1. Interconnections between IS:
- To prevent data intrusion and exfiltration, any interconnections must be inventoried and certified.
- Any interconnections must be secure:
- Use of VPN tunnels with equipment approved by the ANSSI to protect data flows,
- Application of confidentiality, integrity, anti-replay and mutual end authentication measures,
- Filtering upstream flows via external firewalls and downstream through internal firewalls.
- Attack detection: the gateways are equipped with computing attack detection systems, with qualified probes.
2. Nomadic access:
Nomadic access is only allowed on business justification, and must:
- Comply with II 901 safety measures.
- Be integrated into the risk analysis related to registration,
3. Ongoing safety supervision
- Internet access from a sensitive IS is prohibited
- In case of operational necessity, a dedicated IS must be made available to users, ideally via bounce stations and otherwise via siloed proxy servers.
4. Sensitive file management
All files transiting through the Internet must be encrypted using RD-approved solutions or having an ANSSI security visa.
5. Information Zone Partitioning
- The “sensitive” and “common” information must be housed in separate, compartmentalized areas.
- The exchange systems between these zones are supervised: installation of dedicated security mechanisms, specific flow exchange directions according to IS classes, access to the system subject to strict authentication and a unique password.
6. Data protection and traceability
- Implementation of content filtering mechanisms,
- Protection against malicious code,
- Traceability of data in transit, attributable to an identified user.
Naturally, access to RD applications is strictly reserved for RD Information Systems.
Data platform: security mechanisms in accordance with II 901
All providers involved in a RD IS must comply with these rules. This is the case of Suadeo, which integrates advanced data security, integrity and confidentiality mechanisms into its Data platform:
- Advanced data encryption protocols for data in transit or at rest,
- Configuration of security tags (tagging) to categorize data and apply appropriate security rules based on the data handled,
- Marking each data to indicate its level of sensitivity,
- Addition of metadata to further automate the sensitivity level,
- Granular management and control of authenticators and access rights, coupled with single sign-on SSO,
- Role-based permissions management, ensuring that only authorized people can access sensitive data,
- Managing user groups and access policies to ensure security policy consistency and automate access management, reducing non-compliant access related to human error
- Setting password complexity rules,
- Implementation of geographical restrictions on access to data,
- Limitation of the duration of user sessions with automatic lock in case of prolonged inactivity,
- Production of detailed logs for complete traceability: identification of users, nature of operations performed, contextual information related to the location of access,
- Dynamic data masking restricting access to sensitive information according to user permissions,
- Complete and time-stamped logging of the platform’s uses (creation, modification, deletion, export of data),
- Recording of uses in real-time, unchanging audit logs, in accordance with the audit standards required by European and national regulations. This information is verifiable and can be reviewed in the event of an audit or incident,
- Interoperability with monitoring tools and security event information systems (SIEM),
- Automatic alerts (by email, integrated notifications or via APIs) to detect and report any unauthorized access attempt, any abnormal action on the platform or any technical incident (ingestion pipeline failures, anomalies in data flows…),
- Segmentation and partitioning of production, recipe and test environments to ensure isolation of sensitive data and prevent unauthorized interaction.
The Suadeo Self Data Services platform includes a graphical administration interface dedicated to technical users. This interface is separate from the business user interface. The technical team uses it to centrally manage all services, access controls and platform settings.
All these integrated security mechanisms make the Suadeo Self Data Services® platform a reference solution for public and state administrations.
In accordance with regulation II 901, the platform can be integrated into a RD environment, as is currently the case within the Ministry of the Interior.
As they are natively integrated, all these mechanisms are also criteria for choice in the Data projects of private organizations that are fundamentally committed to securing and protecting their data.
[1] Source: ANSSI Guide – Recommendations for Architectures of Sensitive or Restricted Distribution Information Systems Recommendations for Architectures of Sensitive or RD IS | ANSSI